
With the increasing advancement in technology, the need for enhanced security is also growing drastically. To cater to this requirement, organizations are rapidly adopting new and far more sophisticated technologies that help them tackle various security issues and ensure the quality, reliability, and dependency of the software products/features delivered.
Among the various technologies used today to fulfill this requirement, DevSecOps is a prominent one.
In this article, we define the importance of DevSecOps and the process it uses to ensure complete security.
Let’s begin!Introduced to overcome the flaws of traditional security processes implemented in DevOps, DevSecOps helped remove the silos between the development, security, and operations team. It initiated a transformational shift enabling teams to incorporate secure culture, practices, and tools that drive collaboration, agility, and visibility of security into each phase of the DevOps pipeline, mitigating any potential security risks.
The technology uses security as a code culture, where the security tools are embedded within the DevOps lifecycle to automate the process and decrease the issue remediation time to make the product safer and reliable. DevSecOps follows a process where the emphasis is on building a secure foundation into DevOps initiatives, with everyone being responsible for the product's security.
Moreover, it follows the shift-left approach wherein security processes are embedded early into the design/plan phases of software development to provide complete security awareness to the development and operations teams, fulfilling the critical cybersecurity requirements.
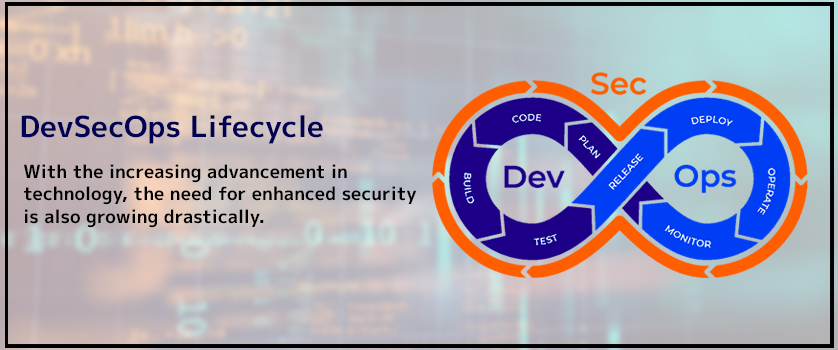
DevOps follows a traditional development cycle that involves phases like Plan, Code, Build, Test, Release, Deploy, Operate, and Monitor. Whereas, in DevSecOps, some distinct security steps are integrated into each of the DevOps development phases for thorough security checks, which help organizations build and deliver increasingly secure products at an accelerated rate.
The first phase of the DevSecOps lifecycle, thread modeling, helps the team assess an application and its surrounding environment to find as many vulnerabilities as possible before attackers do.
By implementing threat modeling within the traditional development process, teams are able to gather a summary of possible attack scenarios, outline the sensitive data workflow, identify vulnerabilities and potential mitigation options.
Like the majority of the processes in DevSecOps, this is also implemented with the help of tools like OWASP Threat Dragon, IriusRisk, ThreatModeler, etc.
After the threat modeling phase, the code is analyzed in the scanning phase to ensure it is secure from security vulnerabilities. This phase involves both manual and automated code review, which helps developers to identify security vulnerabilities and bugs earlier in the software development life cycle.
This phase involves the use of tools like Static Application Software Testing (SAST) and Dynamic Application Security Testing (DAST).
After code analysis, the team reviews all the data and metrics collected from the previous phases to identify security risks. These risks are then compiled based on their severity and priority.
Tools like Klocwork can be used to identify security vulnerabilities within the data and metrics collected.
Once all the security vulnerabilities are identified and organized in the previous phases, the team moves on to the remediation phase, where steps are taken to rectify issues. This involves the use of various SAST tools that suggest solutions for the identified vulnerabilities, errors, and bugs.
This makes it easier for the team to address and rectify the security issues as they arise.
Though last, this is another critical phase of the DevSecOps lifecycle, where the team is responsible for tracking all the identified vulnerabilities, the steps taken to mitigate or eliminate those vulnerabilities, and the overall status of the application’s security. This allows them to make informed data-driven decisions during the software development lifecycle, which further helps them deliver quality and secure products/features to the users.
Apart from tracking the aforementioned aspects, the team can also track and manage the differences between the actual and target metric values, which will allow the organization to experience advancement in operational efficiency across various departments.
Though there is no concrete process for implementing DevSecOps, these steps are usually present. Depending on the complexity and size of your project, your development lifecycle might include some other sequential steps.
To ensure maximum benefits with DevSecOps, the team must follow certain best practices like:
By implementing DevSecOps, organizations can leverage various benefits like:
With security becoming a major concern for the IT industry today, DevSecOps has opened the door for organizations to experience next-level security, efficiency, and reliability. By adopting DevSecOps, organizations can add security to a significant or active part of the Software development life cycle (SDLC) and enjoy benefits like quicker response times from security teams, earlier detection of code vulnerabilities, and enhanced product reliability.
Considering these factors, it is not surprising that organizations in the future will shift from DevOps adoption to DevSecOps.